President's message: Showdown with Shodan
Your Reliable Controls Authorized Dealer can help you achieve your cybersecurity goals.






Building automation systems play an integral role in the health and welfare of the most valuable assets of any organization: their people, and their property. These systems provide automated control of, and human interaction with, mechanical systems that are often complex, expensive, and critical to the operation of facilities while consuming significant energy. Proper design, development and operation of building automation systems is fundamental to the sustainability of the modern built environment.
Largely through the management of information, these systems empower building engineers and facility executives to manage their environment and cultivate their built portfolios.
There is a growing and natural synergy between facility automation and information technology. As these systems trade primarily in facility information, building automation systems increasingly rely upon the Information Technology (IT) infrastructure and systems of the facilities and organizations they serve. (Granzer, Praus, & Kastner, 2010).
This collaborative technology has become known as cyber physical (cyber-physical, or cyberphysical) systems (CPS). A Cyber Physical System, sometimes referred to as embedded systems, is a transdisciplinary approach. A system that merges cybernetics, mechatronics, design and process sciences. CPS represents the realized synergy between physical and software components, particularly between physical systems and internet technologies.
This phenomenon is now increasingly being referred to as IT/OT to highlight the commonalities and convergence of Information Technology (IT) and Operational Technology (OT) systems. Operational Technology (OT) is a relatively recent term used to encompass the direct monitoring and/or control of physical devices, processes and events.
Most current industrial and facility control standards and protocols were defined in the last century, when the TCP/IP protocol suite was expensive and not available for smaller devices common in building automation. However, with the ubiquitous availability of IP network infrastructures today, building automation systems are often a component of facility networks that may be shared with other applications, and may be professionally managed by an IT department. “There is an urgent need for a more IT-friendly solution that is more consistent with standard IT infrastructures” (ASHRAE SSPC 135, 2018).
The information and technology implicit within these shared IT systems are valuable assets that must be protected from vulnerabilities and threats. Because of the standardization of their integration, building automation internetworks should be providing “protection schemes commensurate with, and adhering to, the security controls already established in the IT domain” (Granzer, Praus, & Kastner, 2010).
However, this has traditionally not been the case.
The Washington Post conducted an interview about cybersecurity with executives from an innovative building automation system manufacturer whom revolutionized the industry landscape by bringing building automation systems to the internet. In the interview the executives commented that for more than a decade, “few people gave much thought to the security of commercial control systems on the internet”. They went on to say that “attacks seemed unlikely”, because hackers had not traditionally targeted such systems; concluding that they and their customers “generally assumed that control systems were buffered somewhat by their obscurity” (O’Harrow, 2012).
In a 2015 survey, researchers from IBM found 84 percent of facility managers surveyed reported that their building automation systems are connected to the internet, while just 29 percent had taken action or were in the process of taking action to improve cybersecurity for their internet-connected systems (Snyder, 2014).
Is there any reason for concern?

The principal security threats to BACnet systems are people who, intentionally or by accident, modify a device’s configuration or control parameters (ASHRAE SSPC 135, 2018).
Unauthorized access to a building control system and its data could be used to:
In November 2011, the industrial control system for a waste water treatment plant in South Houston was penetrated when “only a three-character password had been used to protect the system” (BCC, 2011).
A Distributed Denial of Service (DDoS) attack resulted in the loss of heating to two buildings in the city of Lappeenranta in eastern Finland according to a report by local media, the latest example of downstream effects of cyber attacks on connected infrastructure.
According to a published statement from the local IT management firm Valtia, and a report by the local Finnish Communications Regulatory Authority, the attack was noticed after a building automation system used in two properties began issuing strange alarms and could not be remotely accessed. The cause was a sustained denial of service attack that was flooding the building management system with bogus internet traffic, causing it to restart every few minutes, and denying remote administrators at Valtia access to the device. The attack spanned from November 3 to November 4, according to Simo Rounela, the CEO of Valtia. a report by the website Metropolitan.fi.
The result? “The majority of the controlled systems, such as heat distribution, ventilation and hot water went temporarily ‘broken’,” the company said in a statement. To fix it, a technician visited the buildings and removed the affected hardware from the internet until the malicious traffic could be filtered out (Paul, 2016).
In 2013 it was announced that security researchers with Cylance, a cybersecurity consulting firm, were able to hack into building automation system belonging to the Google Wharf 7 facility in Sydney, Australia.
A vulnerability allowed them to remotely access the system’s configuration file, which holds system data including usernames and passwords for logging into operator accounts and controlling the systems they managed. It also allowed them to overwrite files on the device and to gain root access on what amounts to a Windows system with a Java virtual machine running a client software. They identified over 20,000 instances of the same system worldwide (Zetter, K., 2013).
Shodan, a search engine for internet-connected devices designed to raise awareness, identifies nearly 30,000 building automation systems from just one common platform that are exposed to the internet using standard, default IT configurations. A search reveals, almost 20,000 instances in the United States alone, with nearly 2,000 more in Canada, and growing numbers presently exceeding 800 facilities in Australia.
Shodan also identifies nearly 15,000 BACnet systems throughout the world, similarly exposed to the internet, and using the standard, default IT configurations, including the published port reserved for BACnet interoperability. This includes systems that are available numbering more than 9,000 in the United States, 2,000 in Canada, and almost 200 in Australia.
In 2012 the United States Department of Homeland Security (DHS) established the Industrial Control System Cyber Emergency Response Team (ICS-CERT) to combat this growing threat.
According to the U.S. General Accounting Office, the number of cyber incidents involving control systems that were reported to the Department of Homeland Security increased 74 percent from 2011 to 2014, with 245 incidents reported in 2014. In 2017 alone, ICS-CERT received more than 1,000 reports of ICS.

Everyone involved or influenced by the automation of the built environment should be taking the cybersecurity of these systems seriously.
Building operators, facility executives, and portfolio managers, have an obligation to protect their facilities. Engineers, system designers, manufacturers, vendors, contractors, and technicians have an obligation to protect their clients.
ASHRAE is a global society advancing human well-being through sustainable technology for the built environment. AHRAE’s mission is to advance the arts and sciences of heating, ventilating, air conditioning and refrigeration to serve humanity and promote a sustainable world.
How can built environment professionals advance human well-being through sustainable technology as it influences building automation system cybersecurity?
This next step is not an insurmountable obstacle. Building automation systems are already widely accepted in the IT domain. Increasing their standardization and security should only improve their integration into facility IT infrastructures and teams.
Ultimately, each organization should perform an objective assessment of the potential impact to the organization’s assets, and ability to perform its normal business/mission operations in the event of a security breach. A security breach impact assessment is a valuable resource to enable an organization to make an informed selection of appropriate security controls. One important result of such an assessment is the definition of an acceptable balance that delivers the required usability and performance of the building control system while maintaining an appropriate level of security. It is the responsibility of each organization to develop a policy that articulates this balance.
The National Institute of Standards and Technology (NIST) Special Publication (SP) series 800 on Computer Security establishes the principles for Information Technology Security (ITS) best practices and serve as the foundation for the United States Federal Information Processing Standards. In particular, NIST SP 800-27 Engineering Principles for Information Technology Security (A Baseline for Achieving Security), Revision A presents “a list of system-level security principles to be considered in the design, development, and operation of an information system” (Stoneburner, Hayden, & Feringa, 2004). These EP-ITS provide a fundamental foundation to the design, development, and operation of an appropriately secure building automation system.
These publications give us very simple steps to follow.
Hardening is the process of improving the security of an information or computing system by reducing its surface of vulnerability. This is accomplished by trusting only a minimum number of system elements thereby reducing the exposure of vulnerabilities that could be exploited for unauthorized information access and manipulation. Creating an appropriately secure building automation system environment depends upon the requirements and functional expectations of the owner and end-user of the system. The goal of hardening should be to “enhance mission/business capabilities by mitigating…risk to an acceptable level” (Stoneburner, Hayden, & Feringa, 2004).
There is an important subtlety in an effective attitude towards cybersecurity risk that is often overlooked. This realistic strategy is expressed in the National Institute of Standards and Technology Baseline for Achieving Security:
“Previously, risk avoidance was a common IT security goal. That changed as the nature of the risk became better understood. Today, it is recognized that elimination of all risk is not cost-effective. The goal of hardening should be to “enhance mission/business capabilities by mitigating…risk to an acceptable level” (Stoneburner, Hayden, & Feringa, 2004).
To put this into perspective: in the United States, in 2016, there were over 37,000 motor vehicle fatalities. That’s approximately 100 people per day. Yet, for most Americans, driving is an acceptable risk. Even in less than ideal conditions; driving is necessary to the execution of their mission.
When defining an acceptable level of risk, the costs and benefits of protection measures (also known as security controls) should be objectively evaluated. Competing operational needs must be assessed. Usability and performance of the building control system and the protection measures are important considerations when designing and enforcing security controls. The benefits of each security control should provide value commensurate to the direct and indirect costs associated with its implementation and maintenance (Stoneburner, Hayden, & Feringa, 2004).
Like any information system, the purpose of securing a building control system is to preserve the confidentiality, integrity, and availability of data while it is being processed, transmitted and stored (Stoneburner, Hayden, & Feringa, 2004):
We can follow some very simple guidelines to facilitate this protection:
System Design & Configuration
1. Vendor hardening guidelines.
A. Ask for hardening guidelines to be submitted as a qualification.
B. Ensure that the guidelines are followed.
C. Audit the configuration.
2. Network integrity.
A. Deploy on trusted networks.
B. Do not breach the firewall with inbound connections.
C. Use non-standard ports.
D. Dedicated building automation networks.
3. Encryption.
A. Data Transmission.
B. Credential transmission/storage.
C. Deploy a BACnet Virtual Private Network.
4. Contingency and Recovery Plan.
A. System Audits.
Authentication
1. Disable Public Users.
A. Disable/change all default credentials.
2. Assign unique credentials for each user and process.
A. Define user roles and permissions.
B. Implement least privilege.
C. Use credential audits to disable unused accounts.
3. Enforce a password management policy.
A. Use strong passwords.
B. Regularly change passwords.
C. Consider passphrases.
4. Enable auto sign-off after inactivity.
Server Configuration
1. Vendor hardening guidelines.
A. Ask for hardening guidelines to be submitted as a qualification.
B. Ensure that the guidelines are followed.
C. Audit the configuration.
2. Secure the server Operating System.
3. Secure the server software.
4. Maintain the security of the server.
External Influences
1. Implement physical security.
2. Virtual Private Networks.
3. User training.
BACnet is the ASHRAE standard for open protocol building automation. ANSI/ASHRAE Standard 135-2016 A Data Communication Protocol for Building Automation and Control Networks is designed to standardize communications between building automation devices regardless of manufacturers, allowing the interchange of data and interoperation of equipment and systems. This ideal is facilitated through technology that incorporates a few fundamental values including (ASHRAE SSPC 135, 2018):
Some fundamental components of BACnet communication on Ethernet and IP networks are red flags to IT professionals and present challenges to protection schemes commensurate with, and adhering to, the common security controls already established in the IT domain. The traditional BACnet/IP data link:
1. Transmits data in plain-text; placing facility data confidentiality and integrity at risk.
2. Internetwork IP communication requires static IP addresses for BACnet broadcast management.
3. Inbound, firewall penetration and port-forwarding rules.
4. What is perceived to be an outdated transport method.
Penetrating facility firewalls with standard, open protocol, easily accessible requests and responses is a substantial risk to the confidentiality and integrity of facility data; however, access from outside of the trusted Local Area Networks (LAN) is often crucial to the availability of facility data.
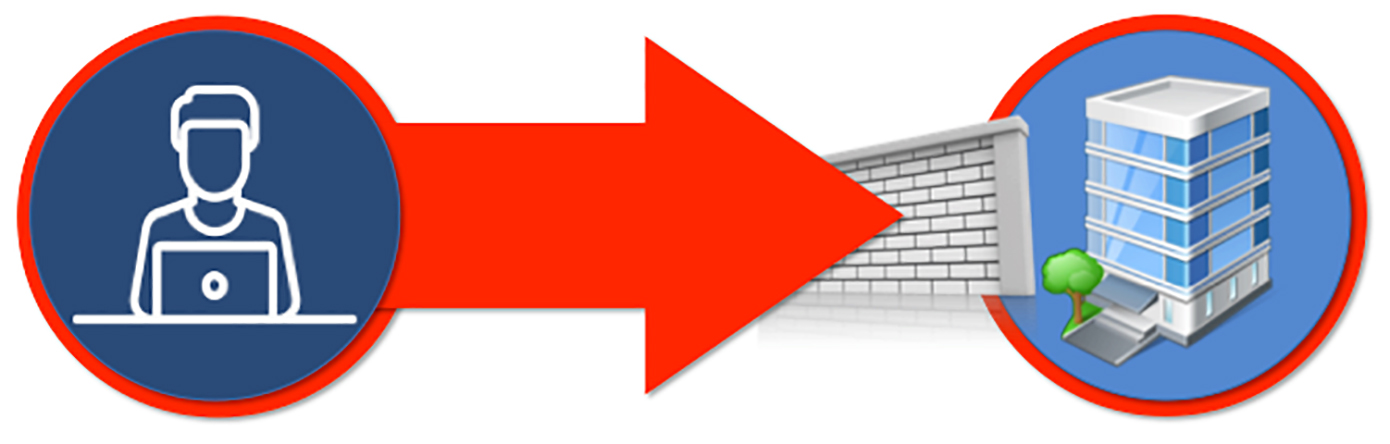
Following the traditional BACnet/IP model for remote connectivity and IP internetwork communication, inbound firewall rules and port forwarding are common.
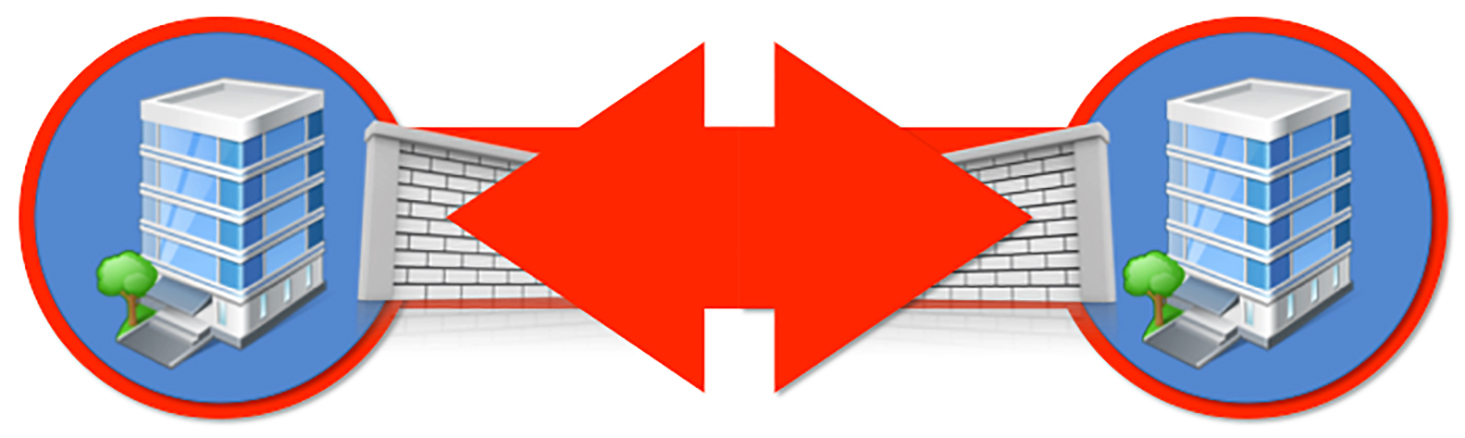
The RC-RemoteAccess® BACnet Virtual Private Network (B/VPN) is expressly designed to strengthen the synergy between BACnet and traditional IT methodologies while providing protection schemes that are inherently commensurate with common security controls already established in the IT domain through the introduction of TLS secured WebSocket connections.
A B/VPN addresses modern IP infrastructure and IT security requirements. The use of Transport Layer Security (TLS) enables the secure exchange of NPDU packets across a wide range of non-managed to tightly managed IT environments. State-of-the-art TLS enables strong information security for BACnet communication.
A B/VPN introduces a new model that eliminates the need for inbound connections through a facility firewall by facilitating secure outbound connections instead.
The B/VPN is based on a logical hub-and-spoke model providing protocol-based connections between client nodes and a server node. The connection is initiated from a client node to the server or hub.
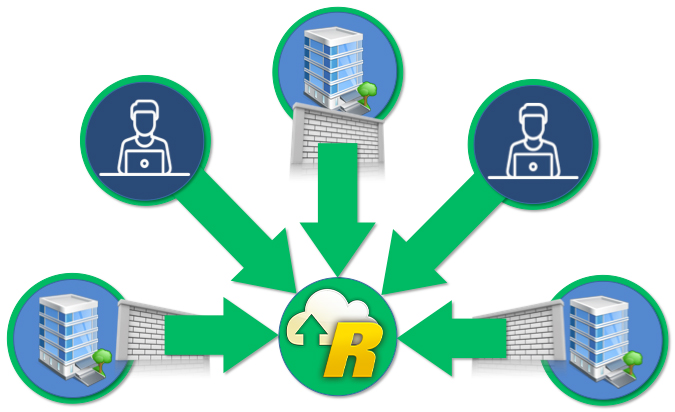
Once the B/VPN logical client/server model is established, the spokes are bi-directional. Through this model, operators and technicians can access their BACnet facilities remotely, and BACnet networks can be combined securely using an established model analogous to a traditional VPN, but purpose designed for BACnet data transmission.
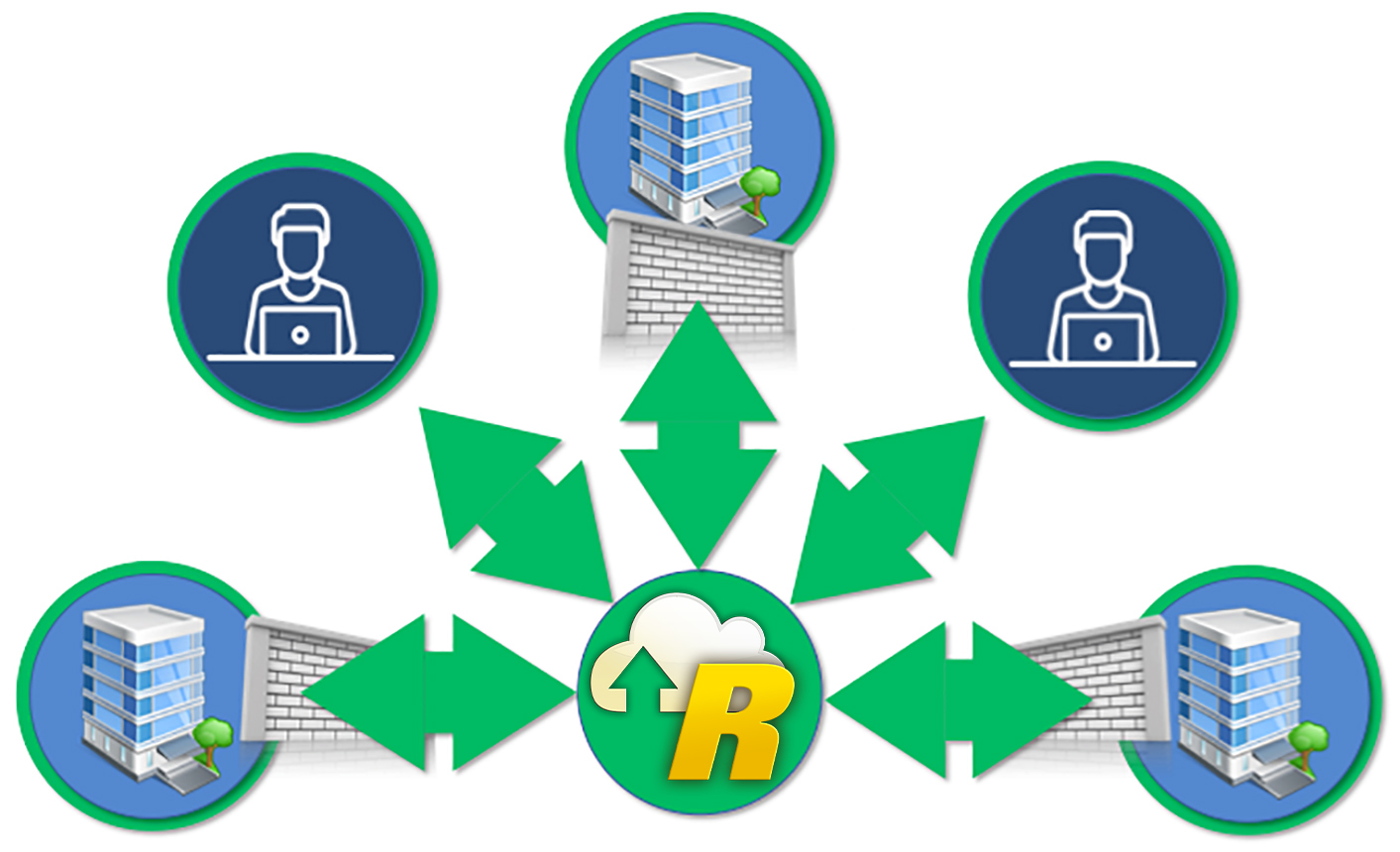
The B/VPN has modernized and revolutionized the integration of BACnet and IT.
Here…wherever here may be. All building automation systems should be appropriately secured. All facilities deserve to be properly protected.

Now.
The goal of hardening should be to “enhance mission/business capabilities by mitigating…risk to an acceptable level” (Stoneburner, Hayden, & Feringa, 2004).
For more information about cybersecurity please refer to the MACH-System Hardening Guide available from the Dealer Support Center (login required).
As influencers and professionals belonging to the built environment industry, we have an obligation to raise awareness for the benefit of our industry, and on behalf of the occupants of the built environment.
BBC. Hackers ‘hit’ US water treatment systems. (2011, November 21). Retrieved January 28, 2018, from http://www.bbc.com/news/technology-15817335
Granzer, W., Praus, F., & Kastner, W. (2010, November). Security in Building Automation Systems. IEEE Transactions on Industrial Electronics, 57(11), 3622-3630. doi:10.1109/TIE.2009.2036033
O’Harrow Jr., R. (2012, July 11). Tridium’s Niagara Framework: Marvel of connectivity illustrates new cyber risks. Retrieved January 28, 2018, from https://www.washingtonpost.com/investigations/tridiums-niagara-framework-marvel-of-connectivity-illustrates-new-cyber-risks/2012/07/11/gJQARJL6dW_story.html?utm_term=.e743b8a75b7c
Paul. IBM Research Calls Out Smart Building Risks. (2016, February 05). Retrieved January 28, 2018, from https://securityledger.com/2016/02/ibm-research-calls-out-smart-building-risks/
Paul. (2016, November 08). Update: Let’s Get Cyberphysical: Internet Attack shuts off the Heat in Finland. Retrieved January 28, 2018, from https://securityledger.com/2016/11/lets-get-cyberphysical-ddos-attack-halts-heating-in-finland/
Snyder, L. (2014, December 17). Hackers Pose Threat To Building Automation Systems - Facilities Management Building Automation Feature. Retrieved January 28, 2018, from http://www.facilitiesnet.com/buildingautomation/article/Hackers-Pose-Threat-To-Building-Automation-Systems--15557?source=part
Stoneburner, G., Hayden, C., & Feringa, A. (2004). SP 800-27 Rev A: Engineering Principles for Information Technology Security (A Baseline for Achieving Security), Revision A. National Institute of Standards and Technology, Information Technology Laboratory: Computer Security Division. Gaithersburg: NIST. Retrieved November 17, 2015, from http://csrc.nist.gov/publications/PubsSPs.html#SP 800
Zetter, K. (2013, June 03). Researchers Hack Building Control System at Google Australia Office. Retrieved January 27, 2018, from https://www.wired.com/2013/05/googles-control-system-hacked/
Zetter, K. (2013, June 03). Vulnerability Lets Hackers Control Building Locks, Electricity, Elevators and More. Retrieved January 28, 2018, from https://www.wired.com/2013/02/tridium-niagara-zero-day/

Your Reliable Controls Authorized Dealer can help you achieve your cybersecurity goals.

Flexible security solutions that also reduce energy consumption.

How does building automation ensure hospitals are safe, secure, comfortable environments for everyone?

Find out how APIs empower you to do more with your building with less effort.

Discover how Liable Controls is bringing relationship-first building automation to South Florida as a new Authorized Dealer.

Explore how our technology automates complex enterprise portfolios.

How does Business Development Executive Sean Roukey help our dealers grow and succeed?

System Mart doesn’t just implement Reliable Controls solutions. It embodies our values of reliability, trust, and long-term commitment. Learn more.